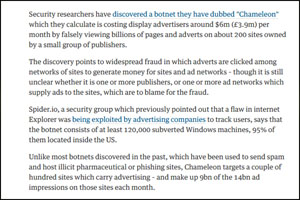
Botnet Scams
With the advent of advanced technology, cybercriminals have become increasingly sophisticated. These tech-savvy perpetrators infiltrate computers, often discreetly siphoning off invaluable data from primary folders and servers. They don’t limit themselves to mere data theft but leverage this stolen information for numerous nefarious activities. Botnet scams, a relatively recent menace, have begun to gain traction. Essentially, 'botnet' stems from the terms 'robot' and 'network', illustrating how malefactors stealthily introduce malware into computers and remotely commandeer them.
Recent FBI disclosures about botnet scams paint a grim picture. Millions of computers globally are succumbing to botnet infections, resulting in colossal data losses for many enterprises. These digital heists typically target high-value data like credit card details, proprietary tech secrets, and even confidential government information. Both individual users and large organizations find themselves grappling with the pervasive threat of botnets.
Botnets aren’t just restricted to computers. With the ubiquity of smartphones, scammers have extended their nefarious activities to mobile devices. Unsuspecting users often receive deceptive text messages with infected attachments. Once accessed, the malware wreaks havoc on their devices. Botnet attacks from certain regions, especially Estonia and Russia, have become notoriously prevalent. Notably, the 'Operation Ghost Click' scam posed a significant challenge even for the FBI. This Trojan, upon infiltration, swiftly expropriates or corrupts vital data, giving hackers unmitigated control.
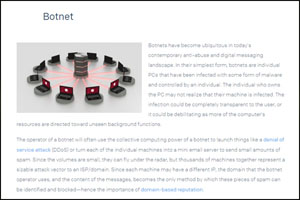
Often, scammers use guile and coercion to make victims unknowingly install malicious software, paving the way for data theft. To fortify your defenses against such breaches, consider the following steps:
- Monitor your computer's performance. An unexpected slowdown could indicate a potential breach.
- Equip your system with cutting-edge antivirus software to ward off malware threats.
- Stay updated on hacker tactics and regularly upgrade your system's security features.
- Avoid storing sensitive information like credit card details and passwords on your computer.
- Report any suspicious cyber activities to the appropriate authorities for immediate action.