Internet Scams
The internet is a rapidly evolving technology, providing ample space for continuous advancement and development. It functions as a network of networks, allowing connections to be established with a simple click. However, within this vast landscape, there exist individuals who exploit this technology to deceive innocent and unsuspecting users through various forms of internet scams. The history of internet scams traces back to earlier times when online users fell victim to deceit under the guise of connectivity.
Spamming
Advices
- Register a complaint with both your internet service provider (ISP) and the spammer's ISP. Ensure that you include the complete header of the junk mail.
- Avoid responding to unsolicited emails, as doing so may inadvertently confirm your email address to the spammer.
- Create a dedicated email address for communication with friends and associates. For interactions with various websites and companies, consider using a free web-based email service such as Yahoo or Hotmail.
Click Video to See About Online Scams
Scammers have become increasingly adept at crafting sophisticated web-based malicious code designed to infiltrate victims' computers or target browser cookies to illicitly access personal information. The core association with internet scams lies in the concept of "identity theft," where scammers exploit various tactics to compromise a user's confidential information. The landscape of internet scams has evolved, taking on diverse forms.
We have curated a compilation of websites dedicated to combating internet scams, offering valuable resources for online users to report scams or seek solutions if they fall victim to fraudulent activities. This comprehensive list aims to empower individuals with the necessary tools and information to navigate the digital landscape safely and securely. Stay informed and take advantage of these platforms to contribute to the collective effort against online scams.
Various forms of Internet scams:
Some real time examples of identity theft:
The provided screenshot serves as an illustration of a female scammer, Cheryl Wright, who received a
72-month prison sentence and a fine of $690,767. Wright was
convicted for engaging in fraudulent activities, specifically filing false tax returns on behalf of
deceased individuals. Her modus operandi involved using
personal identifying information, including social security numbers, belonging to individuals who
had passed away.
This case underscores the severity of identity theft and the misuse of sensitive data for financial
gain. It serves as a stark reminder of the importance of robust
security measures and the need for individuals to remain vigilant against such scams. By staying
informed and adopting proactive practices, one can contribute to
safeguarding personal information in the digital age.
- Tax fraud identity scam:
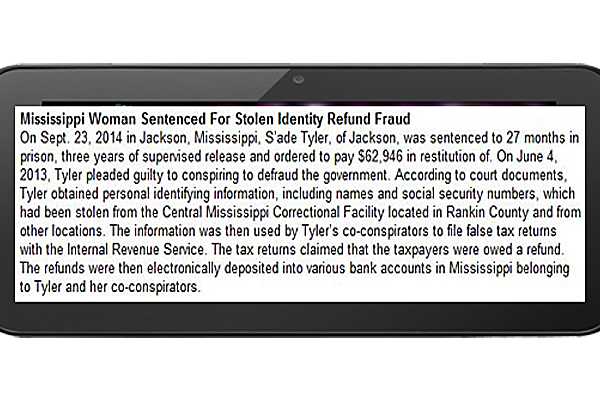
- Here's another case of identity theft involving a female scammer who participated in stealing personal identity information from the Central Mississippi Correctional Facility situated in Rankin County. Teaming up with a co-conspirator, she played a role in the submission of counterfeit tax returns.
- Identity theft scam scheme:
- Kevin Cimeus, a scammer from Florida, received a 156-month prison sentence on September 17, 2014. He was found guilty of engaging in identity theft and tax fraud, wherein he illicitly obtained tax amounts using 2,400 sets of identification information and social security numbers belonging to unsuspecting individuals. This case serves as a stark reminder of the serious consequences associated with identity theft and emphasizes the importance of robust security measures to protect personal information in the digital age. Stay informed and remain vigilant to thwart such fraudulent activities.
- Social security number identity theft scheme:
- Identity fraud or theft persists as a pervasive and widespread form of internet scam orchestrated by scammers. In this type of internet scam, wrongdoers compromise the email account of a specific victim, gaining access to the entire contact list associated with that account. Subsequently, the scammer utilizes this access to send emails from the compromised account, often requesting the recipient to wire money. The recipient, under the false impression that the email is legitimately from a friend, may unknowingly fall victim to the scam. Scammers employ various other methods for identity theft, including the prevalent technique of filing fake tax returns in the name of deceased users. Staying vigilant and adopting robust security practices are essential measures to safeguard oneself against the evolving tactics employed by scammers in the realm of identity theft. Remaining informed about emerging threats and continually updating one's security protocols are crucial components of effective protection in the ever-evolving landscape of online scams.


2. Computer crimes:
3. Credit card fraud:
4. Overpayment fraud:
- With the proliferation of online transactions, scammers are seizing new opportunities and devising diverse ways to exploit users. As online buying and selling gain popularity, scammers are adopting schemes such as the overpayment or advance payment scheme. In this scenario, the scammer attempts to make a purchase from your online store or ecommerce platform, where you advertise items for sale. They intentionally overpay and then request a refund for the excess amount. The underlying strategy involves obtaining the refund by providing a fake check. Unfortunately, the user, upon refunding the extra amount, realizes that no legitimate payment was received from the scammer, resulting in financial loss.
- Overpayment fraud is known by various names that allude to the same type of scam, including check overpayment fraud, overpayment scam, advance fee fraud, and advance payment scam, among others.
How does the scam work?
In my case, I sold a computer on eBay. The buyer requested shipping outside the country and sent a generous payment via PayPal, asking for a refund of the difference after I determined the actual shipping cost. The catch: The PayPal payment notification was a forgery, and the eBay account had been compromised. Falling for the scam would have resulted in the loss of my computer and handing cash to the criminal. It's crucial to be cautious whenever someone overpays you. Don't assume you're in the clear just because your bank processes the check; they can still pursue you to recover the money once they realize it's a fraudulent check.
5. Auction fraud:

Some of the problems in auction fraud are:
- Buyers not receiving the goods at all.
- Sellers not receiving payment
6. Phishing Scam:
Tips to avoid and beware of internet scam:
- Always double-check any email that appears to come from a friend's inbox, especially if it urgently asks for money. Such emails could be from scammers who have hijacked your friend's email account.
- Avoid engaging in online purchases that lack secure connections. Thoroughly research a company before making any transactions with them.
- Never provide social security numbers for online purchases. E-commerce sites do not require this information to complete transactions.
- Secure your computer with anti-spyware, anti-malware, and antivirus software.
- Avoid opening email attachments, as they may contain vulnerable plug-ins that can embed malicious code into your computer.
- Regularly update your computer and operating system to ensure optimal security.
- Disable file-sharing capabilities on your computer.
- Always use a strong password for confidential accounts.
- Verify links sent by banks via email, as phishing attempts may use fake emails to target your personal account.
- Never accept overpayments or advance payments. Legitimate buyers typically pay only the actual amount for the product or service.
- Report any online or internet fraud immediately to prevent further scams by the same perpetrator.
- Recognize that the FBI and FTC take substantial measures to assist victims of internet fraud.