Computer hacking Scams
Understanding Computer Hacking:
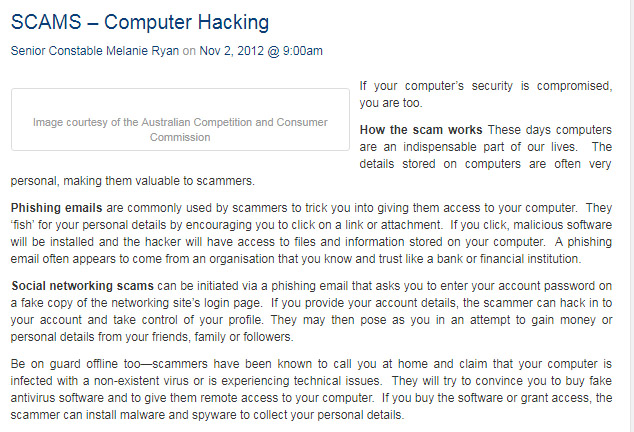
Computer hacking involves unauthorized access into a computer system, aiming to exploit vulnerabilities and breach security protocols. This can encompass techniques that bypass authentication, infiltrate internet users' accounts, databases, software programs, and more, compromising the privacy of a network.
The Deception of Phone Call Hacking:
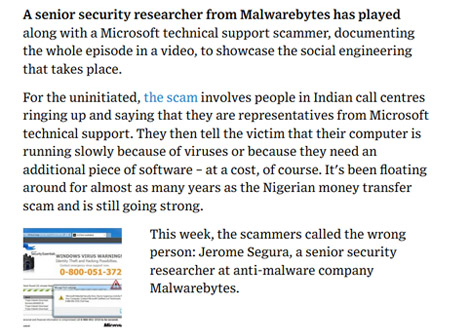
One prevalent method scammers employ to deceive individuals is by initiating a seemingly genuine phone call.
users' accounts, databases, software programs, and more, compromising the privacy of a network.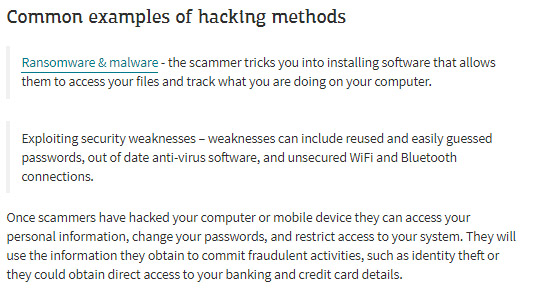
Posing as representatives from established companies like Microsoft, scammers make random calls. They assert that they've detected suspicious viruses on the recipient's computer which, if not addressed, could erase all data and hamper the device's functionality. If a user gets convinced and engages, the scammer further lures them into a trap.
The fraudster then requests remote access to the user's computer. Upon obtaining this, they might modify settings, making the system more susceptible to threats. Additionally, they might trick the victim into signing up for expensive, ineffective online programs or even install malware that discreetly tracks personal, financial, and transactional details.